With the AD Recycle Bin Turned on, What Happens when you Create a User Account with a Password that does not meet the Password Policy?
This was an interesting observation from one of my Windows Server 2012 classes. While working with the AD Recycle bin in a lab, one of my students discovered some interesting accounts that were created. When he created user accounts that did not meet password complexity requirements, an account is temporarily made and then deleted. When a new password is provided that meets the password requirements, then a new account is made.
We discovered this in two places. First off in the Active Directory Administrative Center. This is what caused the initial confusion. Take a look. This is in the Deleted Objects OU.
You can see multiple deleted accounts for Test2 and one for Test3. Test3 is a valid, functioning user account. Using the PowerShell command Get-ADObject –IncludeDeletedObjects –Filter * –Properties ObjectSID we can see that indeed, two accounts were created, with one of them deleted. Notice the RID portion of the SID is different.
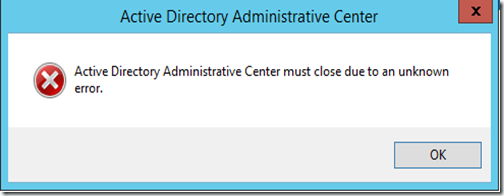
So, here is the big question, Can the deleted version of Test3 be brought back to life. Here is what I received in the AD Administrative Center:
This is when I tried to restore this object to its original location. I expected this. This is what I got when I attempted to restore this object to an alternate location:
A second attempt after reopening the AD Administrative Center yielded the first error. Again this is what I expected. I made one attempt to try and trick AD into restoring this object by changing the real Test3’s UPN and restoring the deleted one, but then I received this:
A restore to a different OU than the original OU and it worked. So, when I logged into a client with a username of Test3, which one worked? The original one did. This is the one with the altered UPN name. I still do not know why this one was selected when both user names are the same. When I used the UPN name of the 2nd Test3 user (The restored one), it successfully logged into that account.
You can’t foul AD, but you can make life difficult for your users. Unless your users are logging in with UPN names, you will have two duking it out to see who can lock the other others account. Make sure you have unique user names in your system.





Comments