You can restrict the type of USB drives that are allowed on your clients be using group policy. I would like to give a word of caution when implementing this. You should consider having a “Support Device List.” This will allow your organization to formally declare what can and cannot be plugged into your USB drives. Without such a list, a constant flow of requests will come in to add more and more devices. It is best to draw the line early and have a formal review process to make sure that the number of supported devices does not become unmanageable.
Settings to control USB Device Access:
| Policy Location | Computer Configuration \ Administrative Templates \ System \ Device Installation \ Device Installation Restriction |
| Policy Name | Prevent installation of devices not described by other policy settings |
| Setting | Enable |
| Configuration | |
| Description | Prevents other USB devices from being installed unless they are specifically allowed in a policy. |
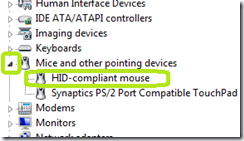
Procedure to get Plug and Play device IDs to allow devices to be used on the clients.
· Plug the device into a client that does not have a policy restricting devices.
· Click Start
· Type Device
· Click Device Manager from the list.
· Expand the category for the device you plugged in and then double click the device
· Click the Details tab.
From here, you need to decide if you are going to allow a class of devices to work on the client. An example of this would be for mice and keyboards. You can also specify a specific device like the USB hard Drive that we will be deploying images on.
For a specific device:
· In the drop down list, select Hardware IDs.
· Copy the information from the first entry. This is the exact hardware ID for this device.
· Browse to the section of the Local Policy below and enter that value in the Configuration of the policy.
· A reboot is required.
The policy below will specify a specific hardware device.
| Policy Location | Computer Configuration \ Administrative Templates \ System \ Device Installation \ Device Installation Restriction |
| Policy Name | Allow installation of devices that match any of these device IDs |
| Setting | Enable |
| Configuration | USBSTOR\DiskWD_____My_Passport_07401003 |
| Description | The configuration is the Hardware ID of the USB Device that you want to allow to connect to the client. Note: This setting can be omitted. To use a USB device, log in as a local administrator and set the policy below labeled Allow administrators to override Device Installation Restriction Policies. |
To allow a class of devices like mice and keyboards
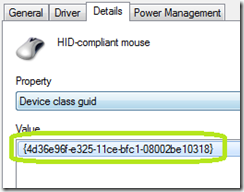
· In the drop down list select Device Class Guid
· Record the guid (curly braces and all).
· Browse to the section of the Local Policy below and enter that value in the Configuration of the policy.
· A reboot is required.
The policy below will specify a specific hardware device.
| Policy Location | Computer Configuration \ Administrative Templates \ System \ Device Installation \ Device Installation Restriction |
| Policy Name | Allow installation of devices that match these device setup classes |
| Setting | Enable |
| Configuration | {4d36e96f-e325-11ce-bfc1-08002be10318} |
| Description | The configuration is the Hardware ID of the USB Device that you want to allow to connect to the client. |
GUID ID for Mouse and Keyboard: {4d36e96f-e325-11ce-bfc1-08002be10318}
| Policy Location | Computer Configuration \ Administrative Templates \ System \ Device Installation \ Device Installation Restriction |
| Policy Name | Allow administrators to override Device Installation Restriction Policies. |
| Setting | Enable |
| Configuration | |
| Description | This policy setting allows you to determine whether members of the Administrators group can install and update the drivers for any device, regardless of other policy settings. If you enable this policy setting, members of the Administrators group can use the Add Hardware wizard or the Update Driver wizard to install and update the drivers for any device. If you enable this policy setting on a remote desktop server, the policy setting affects redirection of the specified devices from a remote desktop client to the remote desktop server. If you disable or do not configure this policy setting, members of the Administrators group are subject to all policy settings that restrict device installation. |

Comments