Here is a good scenario. What if you want to recover an object from the AD Recycle Bin, but its parent OU has been deleted also? Here is a blog article that I wrote a few years ago to help simplify all the PowerShell code that you would have to use. In short, you would have to discover the parent object and restore it before you restore the object that you want.
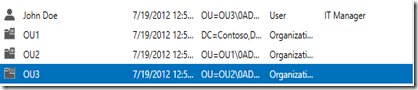
In the image below, you can see that we are looking at the Active Directory Administrative Center. This domain has the AD Recycle Bin turned on and we have 4 objects in the Deleted Objects area. OU1 was the parent with OU2 and its child. OU2 had OU3 as its child. John Doe’s user object was stored in OU3.
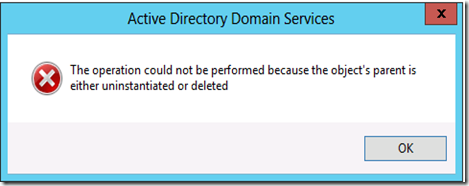
We will start off by right clicking John Doe and selecting Restore. The result is an error.
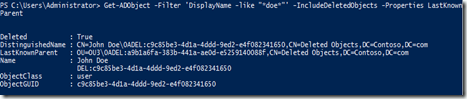
This is because the parent Object of the John Doe object do not exists in Active Directory. They have also been deleted. We can find the parent of john do using PowerShell
Well isn't this a mess? If you look carefully at the LastKnownParent property, you can see the object that needs to be restored first, OU3.
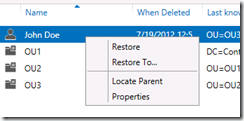
In the AD Administrative Center, you simply need to right click the object that gave you the warning and click Locate Parent.
The Parent object will get the focus.
We could continue to do this until we reach the parent. Once you attempt to locate the parent of OU1, the Focus on the left pane switches to the Domain, which is the parent of OU1. Now you can restore the objects in the following order; OU1, OU2, OU3, John Doe. Not very efficient and what if I wanted to restore just the one object and not 4? Right click on John Doe again and notice the option to Restore To.
Now I can choose where to restore this object to. In this case I selected Users and clicked OK.
Your object is now restored.
In the case of multiple objects that need to be restored, just select them and click Restore or Restore to.


Comments