Many times I have had to talk a remote user through a manual refresh of Group Policy. Depending on the comfort level of the user, this is either a comfortable processes or a highly stressful event…for both of us. You can use PowerShell V3 to invoke a GPUpdate on a remote client. You need to get a few items in order first.
1 – Access to the GroupPolicy module.
Your domain controllers have access to the GroupPolicy module. This is installed by default when they became domain controllers For Windows 8 clients, download RSAT from here.
Once you have access to the module, you need to turn it on. Click Start and Type Programs and Features.
If you are using Windows 8, you will also need to click Settings.
Click Programs and Features
Click Turn Windows Features on or off. This will take a few minutes.
Expand Remote Server Administration Tools / Feature Administration Tools.
Check Group Policy Management Tools.
Click OK.
2 – Configure the Firewall to allow Group Policy Remote Updates.
For Server 2008 R2, you need to manually open the following ports for inbound traffic on your clients.
- TCP RPC dynamic ports, Schedule (Task Scheduler service)
- TCP port 135, RPCSS (Remote Procedure Call service)
- TCP all ports, Winmgmt (Windows Management Instrumentation service)
Windows Server 2012 has a Starter GPO to help you out with this.
Open Server Manager.
Click Tools and select Group Policy Management
Expand the Group Policy Management tree to expose your domain.
Click Starter GPOs. If this is the first time you have used Starter GPOs, you will see this:
Click Create Starter GPOs Folder.
You will now see a list of the Starter GPOs.
Right click where you want to scope this GPO to and then click Create a GPO in this…..
In the New GPO name, type the name that you want.
In the Source Starter GPO drop down box, select Group Policy Remote Update Firewall Ports
Click OK.
You need to let this GPO replicate to your clients before you can invoke a remote GPUpdate.
To test you remote update, log onto a client that you will force the remote update on.
Open PowerShell
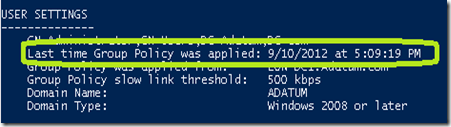
Type GPResult /r and press Enter
Take note of the last time the the GPO was refreshed on either the Computer or User section.
Before proceeding, make sure that you are not attempting to do a remote update on clients in the default Computers container in active directory. Move them to an Organizational Unit first.
Now, go to the server/client that you are going to invoke the remote GPUpdate from.
Open PowerShell.
Type Invoke-GPUpdate –Computer <ComputerName> –Force –RandomDelay 0 and press Enter. Replace <ComputerName> with the name of the remote client.
This will create a scheduled task on the remote client. It will execute immediately with the –RandomDelay parameter set to 0. The user will see a command window pop up as shown below. It will close automatically.
The remote update is now completed.
If you run a GPResult /r on the client, you will see that it has been updated.







Comments
Thank you, Tom
For Windows 2K R2, you will need to test it. I have taken down all my 2008 R2 servers. of course any client that a GPO applies to with settings that client has a client side extension for will be applied.
Jason