You can expand the functionality of the AD Recycle Bin to your Active Directory Lightweight Directory Services (AD LDS) deployments. This example assumes that we have an AD LDS instance called ‘App1’. It will be on a server called ‘MCT-1’ in a domain called ‘MCTNET.com’. We can attach to it on port 53414. The application partition is ‘CN=App1,DC=MCTNET,DC=COM’
On the server hosting the AD LDS instance, open PowerShell.
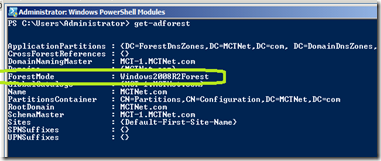
First verify that your Forest functional level is Windows Server 2008 R2.
Type Get AD-Forest and press enter. You can see from the results below that we are at the correct forest functional level.
Open a command prompt with administrative credentials.
Change your directory to c:\Windows\Adam.
Type Ldifde.exe –i –f MS-ADAM-Upgrade-2.ldf –s MCT-1:53414 –b administrator MCTNET Pa$$w0rd –j . –$ adamschema.cat
For your environment replace:
MCT-1 with the name of your server.
53414 with the port number of the AD LDS instance you are turning the AD Recycle bin on.
MCTNET with your domain name
Change Pa$$w0rd to the password for the account being used.

This will upgrade the schema of your AD LDS.
We will now be able to recover objects that are deleted from AD LDS from this point forward. Any objects there were deleted prior to the the AD Recycle Bin being applied to your AD LDS instance will not be recoverable. Also, you will not be able to recover objects from other instances of AD LDS until you run the above procedure on them.
In my AD LDS instance, I deleted two user objects; Barney and Bert. We now need to bind to the AD LDS instance to fid our deleted objects.
For a command prompt with elevated privileges, type LDP and press Enter.
In the LDP window, click Options \ Controls
From the Load Predefined drop down box, select Return deleted objects.

Click OK to close the Controls window.
In the LDP window, click Connection \ Connect…
Provide the server name and the port to connect to the AD LDP Instance.
Click OK

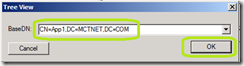
Click View \ Tree.
In the Tree View window, enter the BaseDN of the AD LDS instance. In our case it is CN=App1,DC=MCTNET,CD=COM
Click OK
In the LDP window, click Connection \ Bind
Click OK to close the BIND window.
In the LDP Window, expand your AD LDS instance.
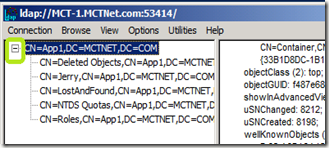
Double click CN=Deleted Objects,CN=App1,DC=MCTNET,DC=COM
You will now see the objects that are being held in the Active Directory Recycle Bin.

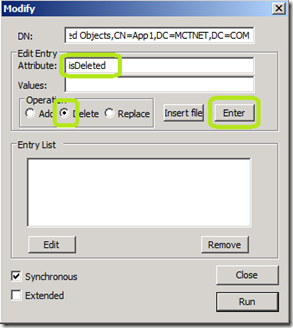
Right click the object that you want to recover and select Modify.
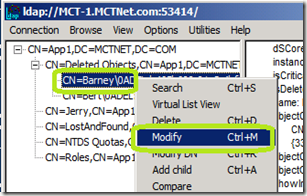
In the Attribute: field, click isDeleted
In the Operation section, select Delete
Click Enter.
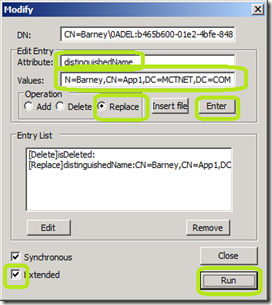
In the Attribute type distinguishedName.
In the Values field, type the Distinguished Name of the object that you want to recover. In our case, it is CN=Barney,CN=App1,DC=MCTNET,DC=COM.
In the Operation area, select Replace
At the bottom left of the Modify window, check Extended.
Click Run
Click Close
If you look in the LDP window, you will see something similar to this:

If you open your AD LDS instance in the ADSI Editor, you will see that your object, Barney, has been restored.

On the server hosting the AD LDS instance, open PowerShell.
First verify that your Forest functional level is Windows Server 2008 R2.
Type Get AD-Forest and press enter. You can see from the results below that we are at the correct forest functional level.

Open a command prompt with administrative credentials.
Change your directory to c:\Windows\Adam.
Type Ldifde.exe –i –f MS-ADAM-Upgrade-2.ldf –s MCT-1:53414 –b administrator MCTNET Pa$$w0rd –j . –$ adamschema.cat
For your environment replace:
MCT-1 with the name of your server.
53414 with the port number of the AD LDS instance you are turning the AD Recycle bin on.
MCTNET with your domain name
Change Pa$$w0rd to the password for the account being used.

This will upgrade the schema of your AD LDS.
We will now be able to recover objects that are deleted from AD LDS from this point forward. Any objects there were deleted prior to the the AD Recycle Bin being applied to your AD LDS instance will not be recoverable. Also, you will not be able to recover objects from other instances of AD LDS until you run the above procedure on them.
In my AD LDS instance, I deleted two user objects; Barney and Bert. We now need to bind to the AD LDS instance to fid our deleted objects.
For a command prompt with elevated privileges, type LDP and press Enter.
In the LDP window, click Options \ Controls
From the Load Predefined drop down box, select Return deleted objects.

Click OK to close the Controls window.
In the LDP window, click Connection \ Connect…
Provide the server name and the port to connect to the AD LDP Instance.
Click OK

Click View \ Tree.
In the Tree View window, enter the BaseDN of the AD LDS instance. In our case it is CN=App1,DC=MCTNET,CD=COM
Click OK

In the LDP window, click Connection \ Bind
Click OK to close the BIND window.
In the LDP Window, expand your AD LDS instance.

Double click CN=Deleted Objects,CN=App1,DC=MCTNET,DC=COM
You will now see the objects that are being held in the Active Directory Recycle Bin.

Right click the object that you want to recover and select Modify.

In the Attribute: field, click isDeleted
In the Operation section, select Delete
Click Enter.

In the Attribute type distinguishedName.
In the Values field, type the Distinguished Name of the object that you want to recover. In our case, it is CN=Barney,CN=App1,DC=MCTNET,DC=COM.
In the Operation area, select Replace
At the bottom left of the Modify window, check Extended.
Click Run

Click Close
If you look in the LDP window, you will see something similar to this:

If you open your AD LDS instance in the ADSI Editor, you will see that your object, Barney, has been restored.

Comments
But when we restore a OU, its children are not restored. We must restore them one by one.
Do you know how we could make the restore recursive, somewhat using the lastKnowParent attribute ?