In some cases you may want to manually start an deduplication process on your Windows Server 2012 storage devices that are configured for data deduplication.
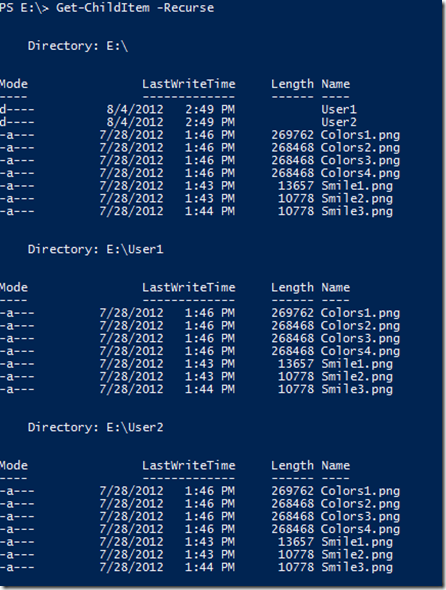
Here we see the same set of files located in three different areas of our e: drive.
To do this, utilize PowerShell.
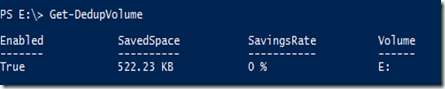
Type Get-DedupVolume
Since we have not performed any deduplication, we do not have any savings.
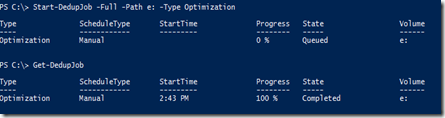
Type: Start-DedupJob –Full –Path e: -Type Optimization
You can get the results by typing Get-DedupJob
The Data Deduplication Service is set to manual because it is either activated via a scheduled task or by PowerShell
By executing Get-DedupStatus –Path e:
Since only files that are greater than 32KB can be optimized by data deduplication, only the files that start with Colors will be processed. The total size of these files are 1053KB per instance. The SavedSpace attribute reflects the removed duplicate data plus the reference pointers for the removed data to a full copy of that data.

Comments
Thanks a lot!
Thanks!!
:)