To test this theory, I created a Snapshot in Hyper-V of a Windows 7 Client. Once I completed this I had Active Directory reset the password to the client. Next I applied the snapshot that I just took to create a disjointed account.
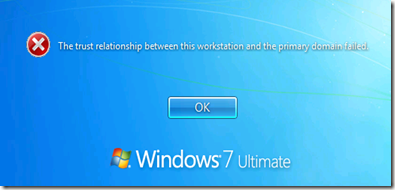
When an attempt to log in is made, this is the error:
The question from class is if I put this client in a workgroup, and then back in a domain, will it have the same SID?
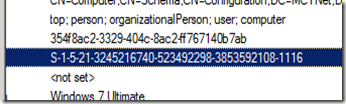
First off, I went into Active Directory and recorded the SID for the clients computer object.
Next I logged in as the local administrator on the client and first put the client in a workgroup, and then back in the domain. One thing that I did notice during this process. Even though the computer could not create a secure channel to the domain controller, when I took it off the network, the computers object was disabled.
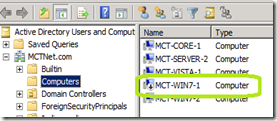
Once the client was joined to the network, its account re-enabled.
Also, the SID was reused.

On a side note. This client was used previously to test the ability for a standard user to add a client to the domain without Domain Administrator credentials. In that process, the users SID was recorded in the computer objects ms-DS-CreatorSID. Even thought I rejoined the client to the network using a Domain Admin account, the original user who added this client to the domain still has their SID listed in the ms-DS-CreatorSID attribute of the clients account.
When an attempt to log in is made, this is the error:

The question from class is if I put this client in a workgroup, and then back in a domain, will it have the same SID?
First off, I went into Active Directory and recorded the SID for the clients computer object.

Next I logged in as the local administrator on the client and first put the client in a workgroup, and then back in the domain. One thing that I did notice during this process. Even though the computer could not create a secure channel to the domain controller, when I took it off the network, the computers object was disabled.

Once the client was joined to the network, its account re-enabled.
Also, the SID was reused.

On a side note. This client was used previously to test the ability for a standard user to add a client to the domain without Domain Administrator credentials. In that process, the users SID was recorded in the computer objects ms-DS-CreatorSID. Even thought I rejoined the client to the network using a Domain Admin account, the original user who added this client to the domain still has their SID listed in the ms-DS-CreatorSID attribute of the clients account.
Comments