The network adapters on a Windows 7 client are configured for router discovery for automatic IP addressing for the IPv6 protocol. To configure your clients to for DHCPv6, you need to disable the router discovery and enable the Managed Address flag on the NIC. To do this, you must log into each client and execute the following commands.
netsh int ipv6 set int Interface_Index RouterDiscovery=Disabled
netsh int ipv6 set int Interface_Index ManagedAddress=Enable
Scale this for domains with thousands of clients of multiple NICs and you have a management problem. This clearly presents a challenge. The set of tasks below will help you to set this configuration across your entire domain in a much more time efficient manner.
To accomplish this, we are going to use a combination of Group Policy and PowerShell V2. What this task entails is to configure your servers to allow you to utilize the PowerShell remoting features to connect to each client, and then run the necessary commands to configure each NIC on each client for DHCPv6.
Step 1, Allow your servers to receive PowerShell remote commands
You can do this in one of two ways. For just a few clients, you can log in as an Administrator and run WinRM QuickConfig. Press Y and Enter when prompted.
For many clients, you will want to do this via group policy.
Open up Group Policy Management.
Expand your Forest / Domains / DomainName
Right Click Group Policy Object and click New.
Provide a name for this GPO. For this demonstration, I named mine PSRemoteSetup.
Right click your GPO and click Edit.
Expand Computer Configuration / Policies / Administrative Templates / Windows Components / Windows Remote Management (WinRM) / WinRM Service.
Open Allow automatic configuration of listeners
- Set this policy to Enable
- Enter * in IPv4 filter:
- Enter * in IPv6 filter:
- Click OK
Expand Computer Configuration / Policies / Windows Settings / Security Settings / Windows Firewall with Advanced Security / Windows Firewall with Advanced Security
- Right click Inbound Rules and select New Rule.
- Select Predefined.
- In the drop down box, select Windows Remote Management
- Click Next
- Check only Windows Remote Management (HTTP-In)
- Click Next.
- Select Allow the connection.
- Click Finish
If this policy is going to be applied to only Windows Server 2008 servers, exit Group Policy Management Editor and move on to step 2.
If this policy is going to be applied to Windows Vista or Windows 7 clients, we need to enable one more Group Policy.
- Expand Computer Configuration / Policies / Windows Settings / Security Settings / System Services
- Double click Windows Remote Management (WS-Management)
- Check Define this policy setting
- Select Automatic
- Click OK
- Exit Group Policy Management Editor and move on to step 2.
Step 2
Now, link this GPO to the OUs that contain the servers and clients that you want to be able to remotely manage with PowerShell. You can do this by right clicking the OU you want this GPO to manage can click Link an Existing GPO…
Click PSRemoteSetup and click OK
Step 3 involves creating PowerShell code that first extracts the list of servers from Active Directory
Open the PowerShell ISE. This can be done by typing in PowerShell on the Windows 7/Server 2008 R2 search line. It is also located at Start \ Accessories \ Windows PowerShell. Right click Windows PowerShell ISE and select Run as administrator. This is because you must have administrative access to execute the commands in the script we will be using.
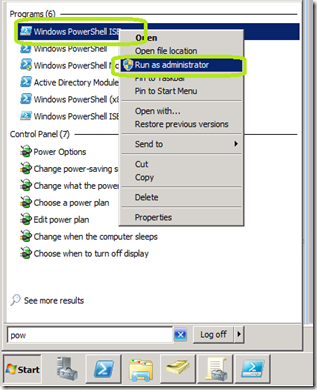
The ISE allows us to easily build multi line scripts with ease as compared to the script building process of PowerShell v1.0
We also need to enable the execution of scripts. For now, type Set-ExecutionPolicy Unrestricted and then click Yes. This allows for this ISE to execute any script we give it. Of course, follow the security guidelines of your organization when it comes the Execution Policy for PowerShell.
We are now ready to start scripting. Type this code in the ISE
# ===================================================
# Script Name: IPv6_Config_Domain.ps1
# Author: Jason A. Yoder, MCT
# Website: www.MCTExpert.com
# Blogsite: www.MCTExpert.Blogspot.com
#
# Script Purpose:
# This script will allow network administrators
# to access the client in their Windows Domain
# and set the IPv6 attributes on all network
# adapters to use DHCP for their configuration.
#
# Requirements:
# - OS: Windows 7, Windows Server 2008 R2
# Vista if PowerShell V2 is installed.
#
# - The ISE (or shell environment) must be
# started with administrative rights.
#
# - All Clients must have PowerShell V2 installed.
#
# - All clients must be configured for PowerShell
# remote management.
#
# - Client or server that this is ran from must have
# RSAT installed.
#
# ===================================================
$ErrorActionPreference ="stop"
#$ErrorActionPreference ="SilentlyContinue"
# Import in the Active Directory module.
Import-Module ActiveDirectory
# Display script title information on the screen.
Write-Host "Script: IPv6_Config_Domain.ps1.....Starting"
# Add to this comma separated list, the FQDN of each OU
# that holds clients that you want to configure.
[array] $OUList = "OU=clients,DC=MCTNET,DC=com"
#Begin cycling through the list or OUs.
ForEach ($OUPath in $OUList){
#Create a list of clients from the OU to configure.
[array] $ServerList = Get-ADComputer -Filter * -SearchBase $OUPath
# Cycle through the list of clients and execute the
# configuration changes.
ForEach ($Name in $ServerList){
Invoke-Command -ScriptBlock{
# Enumerate the list of all NICs on the client.
[array] $IndexList = invoke-Command {netsh int ipv6 show int}
# Determine the number of text lines returned from
# the previous command. The data starts on record
# number 3.
$SizeOfList = $IndexList | Measure-Object
# Begin cycling through the returned data and
# extract the NICs Index numbers
For($i=3; $i -le $SizeOfList.count-2; $i++)
{
# Split each line of the returned array into an array
# of characters
[array] $CharArray = $IndexList[$i].ToCharArray()
# Join the 2nd and 3rd records into a integer. This
# integer represents the Index value for the NIC
# that is being examined.
$IndexNum=$CharArray[0..4]
$Int = $IndexNum[1]+$IndexNum[2]
$Int = [int]$Int
# Use this set of code to enable Router Discovery
#$IPv6String1 = invoke-command {netsh int ipv6 set int $int RouterDiscovery=enable}
#$IPv6String2 = Invoke-Command {netsh int ipv6 set int $int managedaddress=disabled}
# Use this set of code to disable Router Discovery and
# turn on DHCPv6.
$IPv6String1 = invoke-command {netsh int ipv6 set int $int RouterDiscovery=Disabled}
$IPv6String2 = Invoke-Command {netsh int ipv6 set int $int managedaddress=enable}
# Execute the code in the strings.
Write-Host "Adapter: $Int"
$IPv6String1
$IPv6String2
}
} -ComputerName $Name.name -AsJob -JobName "IPv6 Configuration"
If ($? -eq $False) {
Write-Host -fore Red -back Yellow "$Name.name is offline"}
}
}
Write-Host Script: IPv6_Config_Domain.ps1...Completed
In the opening comments section, take note of the requirements. They must be met before this script will run. This script utilizes the new remoting functionality of PowerShell V2. Two items you should note here. This script will configure each network interface on each client that it touches. If this is not desirable, you will have to add the intelligence into the code to change only the NICs that you want to change. Also, if a client is offline, it will not receive the configuration. After the script completes, look through the output to see any clients that were offline. They will be displayed with red text on yellow.
Should you have clients that were not online when this script was executed, you can execute it again later. There will not be any adverse effects if it is ran on a client that it has already configured. Notice that there is code to enable Router Discovery should you want to switch back. Just enable that code and comment out the code to enable DHCPv6.
netsh int ipv6 set int Interface_Index RouterDiscovery=Disabled
netsh int ipv6 set int Interface_Index ManagedAddress=Enable
Scale this for domains with thousands of clients of multiple NICs and you have a management problem. This clearly presents a challenge. The set of tasks below will help you to set this configuration across your entire domain in a much more time efficient manner.
To accomplish this, we are going to use a combination of Group Policy and PowerShell V2. What this task entails is to configure your servers to allow you to utilize the PowerShell remoting features to connect to each client, and then run the necessary commands to configure each NIC on each client for DHCPv6.
Step 1, Allow your servers to receive PowerShell remote commands
You can do this in one of two ways. For just a few clients, you can log in as an Administrator and run WinRM QuickConfig. Press Y and Enter when prompted.
For many clients, you will want to do this via group policy.
Open up Group Policy Management.
Expand your Forest / Domains / DomainName
Right Click Group Policy Object and click New.
Provide a name for this GPO. For this demonstration, I named mine PSRemoteSetup.
Right click your GPO and click Edit.
Expand Computer Configuration / Policies / Administrative Templates / Windows Components / Windows Remote Management (WinRM) / WinRM Service.
Open Allow automatic configuration of listeners
- Set this policy to Enable
- Enter * in IPv4 filter:
- Enter * in IPv6 filter:
- Click OK
Expand Computer Configuration / Policies / Windows Settings / Security Settings / Windows Firewall with Advanced Security / Windows Firewall with Advanced Security
- Right click Inbound Rules and select New Rule.
- Select Predefined.
- In the drop down box, select Windows Remote Management
- Click Next
- Check only Windows Remote Management (HTTP-In)
- Click Next.
- Select Allow the connection.
- Click Finish
If this policy is going to be applied to only Windows Server 2008 servers, exit Group Policy Management Editor and move on to step 2.
If this policy is going to be applied to Windows Vista or Windows 7 clients, we need to enable one more Group Policy.
- Expand Computer Configuration / Policies / Windows Settings / Security Settings / System Services
- Double click Windows Remote Management (WS-Management)
- Check Define this policy setting
- Select Automatic
- Click OK
- Exit Group Policy Management Editor and move on to step 2.
Step 2
Now, link this GPO to the OUs that contain the servers and clients that you want to be able to remotely manage with PowerShell. You can do this by right clicking the OU you want this GPO to manage can click Link an Existing GPO…
Click PSRemoteSetup and click OK
Step 3 involves creating PowerShell code that first extracts the list of servers from Active Directory
Open the PowerShell ISE. This can be done by typing in PowerShell on the Windows 7/Server 2008 R2 search line. It is also located at Start \ Accessories \ Windows PowerShell. Right click Windows PowerShell ISE and select Run as administrator. This is because you must have administrative access to execute the commands in the script we will be using.

The ISE allows us to easily build multi line scripts with ease as compared to the script building process of PowerShell v1.0
We also need to enable the execution of scripts. For now, type Set-ExecutionPolicy Unrestricted and then click Yes. This allows for this ISE to execute any script we give it. Of course, follow the security guidelines of your organization when it comes the Execution Policy for PowerShell.
We are now ready to start scripting. Type this code in the ISE
# ===================================================
# Script Name: IPv6_Config_Domain.ps1
# Author: Jason A. Yoder, MCT
# Website: www.MCTExpert.com
# Blogsite: www.MCTExpert.Blogspot.com
#
# Script Purpose:
# This script will allow network administrators
# to access the client in their Windows Domain
# and set the IPv6 attributes on all network
# adapters to use DHCP for their configuration.
#
# Requirements:
# - OS: Windows 7, Windows Server 2008 R2
# Vista if PowerShell V2 is installed.
#
# - The ISE (or shell environment) must be
# started with administrative rights.
#
# - All Clients must have PowerShell V2 installed.
#
# - All clients must be configured for PowerShell
# remote management.
#
# - Client or server that this is ran from must have
# RSAT installed.
#
# ===================================================
$ErrorActionPreference ="stop"
#$ErrorActionPreference ="SilentlyContinue"
# Import in the Active Directory module.
Import-Module ActiveDirectory
# Display script title information on the screen.
Write-Host "Script: IPv6_Config_Domain.ps1.....Starting"
# Add to this comma separated list, the FQDN of each OU
# that holds clients that you want to configure.
[array] $OUList = "OU=clients,DC=MCTNET,DC=com"
#Begin cycling through the list or OUs.
ForEach ($OUPath in $OUList){
#Create a list of clients from the OU to configure.
[array] $ServerList = Get-ADComputer -Filter * -SearchBase $OUPath
# Cycle through the list of clients and execute the
# configuration changes.
ForEach ($Name in $ServerList){
Invoke-Command -ScriptBlock{
# Enumerate the list of all NICs on the client.
[array] $IndexList = invoke-Command {netsh int ipv6 show int}
# Determine the number of text lines returned from
# the previous command. The data starts on record
# number 3.
$SizeOfList = $IndexList | Measure-Object
# Begin cycling through the returned data and
# extract the NICs Index numbers
For($i=3; $i -le $SizeOfList.count-2; $i++)
{
# Split each line of the returned array into an array
# of characters
[array] $CharArray = $IndexList[$i].ToCharArray()
# Join the 2nd and 3rd records into a integer. This
# integer represents the Index value for the NIC
# that is being examined.
$IndexNum=$CharArray[0..4]
$Int = $IndexNum[1]+$IndexNum[2]
$Int = [int]$Int
# Use this set of code to enable Router Discovery
#$IPv6String1 = invoke-command {netsh int ipv6 set int $int RouterDiscovery=enable}
#$IPv6String2 = Invoke-Command {netsh int ipv6 set int $int managedaddress=disabled}
# Use this set of code to disable Router Discovery and
# turn on DHCPv6.
$IPv6String1 = invoke-command {netsh int ipv6 set int $int RouterDiscovery=Disabled}
$IPv6String2 = Invoke-Command {netsh int ipv6 set int $int managedaddress=enable}
# Execute the code in the strings.
Write-Host "Adapter: $Int"
$IPv6String1
$IPv6String2
}
} -ComputerName $Name.name -AsJob -JobName "IPv6 Configuration"
If ($? -eq $False) {
Write-Host -fore Red -back Yellow "$Name.name is offline"}
}
}
Write-Host Script: IPv6_Config_Domain.ps1...Completed
In the opening comments section, take note of the requirements. They must be met before this script will run. This script utilizes the new remoting functionality of PowerShell V2. Two items you should note here. This script will configure each network interface on each client that it touches. If this is not desirable, you will have to add the intelligence into the code to change only the NICs that you want to change. Also, if a client is offline, it will not receive the configuration. After the script completes, look through the output to see any clients that were offline. They will be displayed with red text on yellow.
Should you have clients that were not online when this script was executed, you can execute it again later. There will not be any adverse effects if it is ran on a client that it has already configured. Notice that there is code to enable Router Discovery should you want to switch back. Just enable that code and comment out the code to enable DHCPv6.
Comments